Identity and Access Management
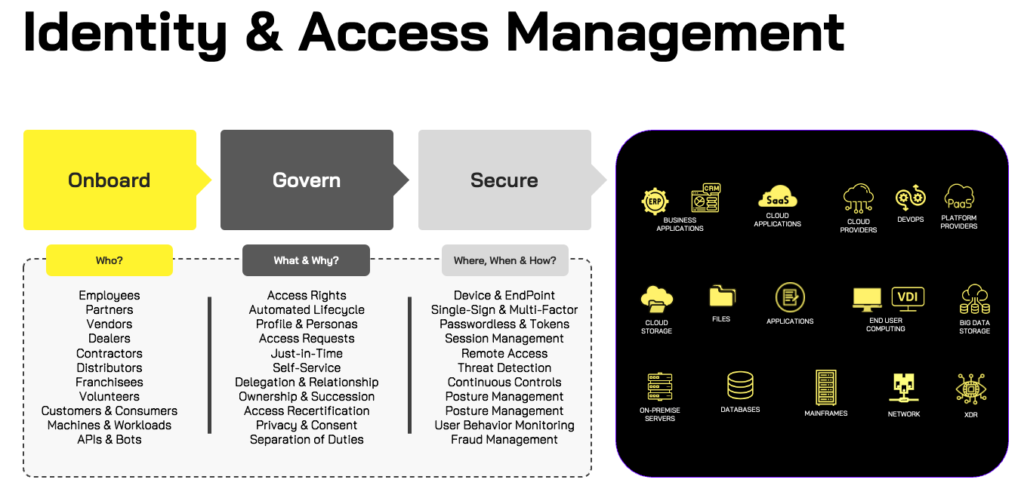
Identity & Access Management
Assess, Modernize, Implement and Manage your Identity & Access Management infrastructure with Abira’s certified IAM Professionals and Trusted Partners.
Looking to replace a legacy solution, mitigate cyber-risk, comply with regulatory controls, enforce least privileged access or align with a Zero-Trust framework? Then look no further as Abira’s renowned Identity & Access Management Programs have helped organizations secure their hybrid enterprise and reduce cyber insurance premiums.
From Advisory and Implementation, to Integration & Managed Services, our team of skilled and certified architects, engineers and business analysts will help assess & recommend, design & architect, or revive and reboot a failed IAM program.
Our core strengths span across Workforce & Customer Access Management, Privileged & Cloud Identity Management, and Identity Governance.
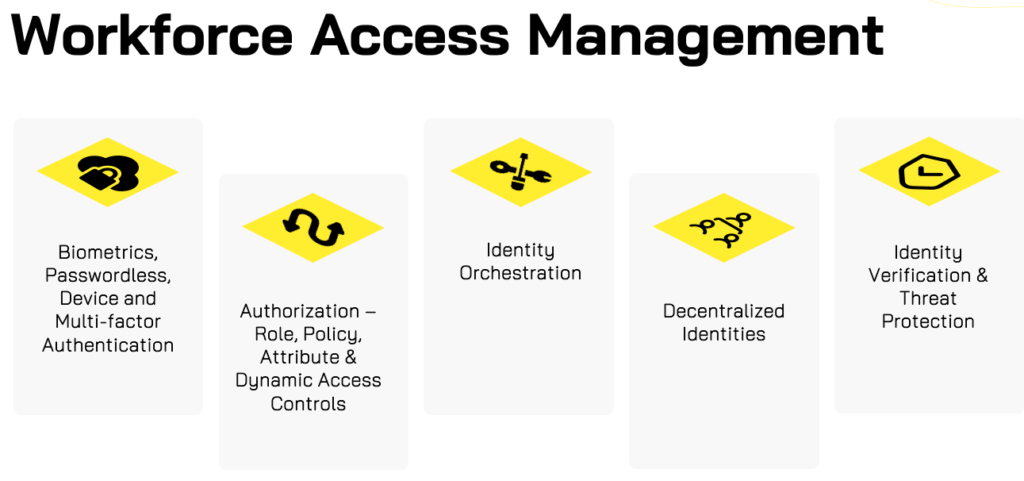
Workforce Identity & Access Management
Enforce & Enable Secure, Seamless and Frictionless access to your Hybrid Enterprise for your internal employees, business partners, vendors, contractors, and other 3rd party Identities. Ensure least-privileged access based on Attributes, Roles, Rules and Dynamic Authorization policies to On-premise, SaaS, IaaS and PaaS end-points with built-in continuous threat detection and remediation. Our team of certified professionals can help implement and manage your Microsoft, Okta, Ping and other Workforce enabled platforms alongside phishing resistant and risk-based MFA providers like Hypr, BeyondIdentity & 1Kosmos to ensure the right people have access to the right resources at the right time.
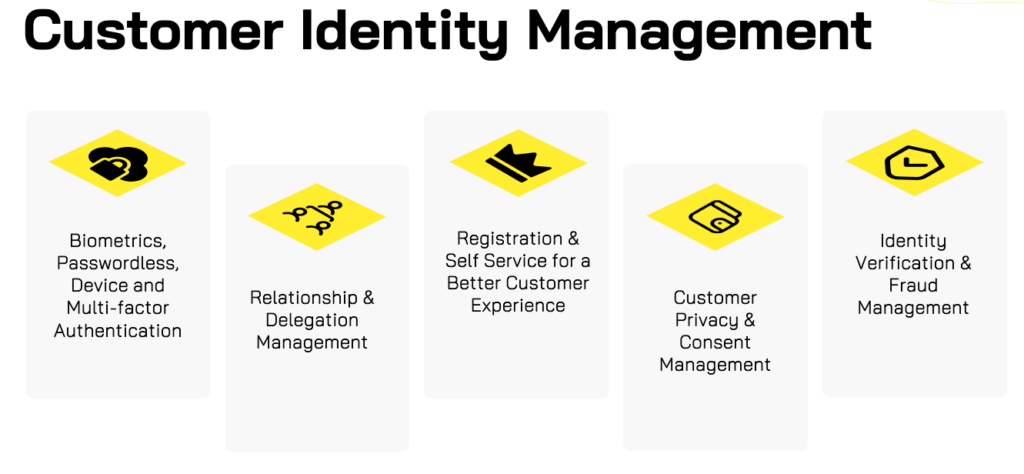
Customer Identity & Access Management
Delight your customer and provide a frictionless onmi-channel experience, with improved self-registration, progressive profiling and password-less authentication.
As organizations move towards a decentralized Web3 internet with anonymous, BYOI & social logins, our team of experts can assist with implementation strategies aimed at centralizing administration, providing for relationship management and unified integration across customer-facing applications. With identity verification and fraud detection capabilities seamlessly integrated into the platform, Abira’s CIAM implementations ensure a smooth customer experience alongside strong privacy protection, resulting in increased revenue and decreased attrition.
Our team of experts are certified on Okta/Auth0, Ping, Strivacity, Microsoft and other CIAM solutions
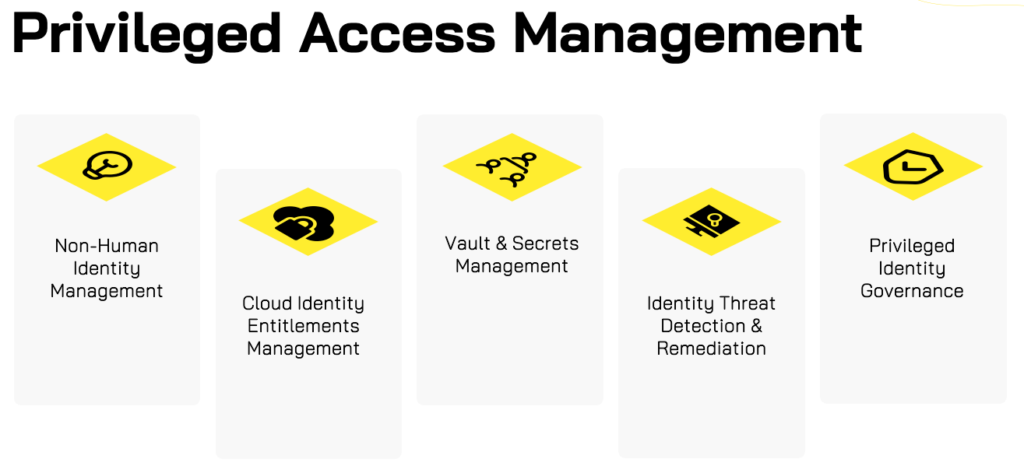
Privileged and Cloud Identity Management
Establishing a least Privileged, Just-In-Time & Credential-less approach is a must for organizations moving towards a security first-compliance later zero-standing privilege model.
Implementing PAM to secure privileged, sensitive & critical access to meet regulatory controls, or lower your cyber insurance premiums? Abira’s certified team of PAM experts help develop strategies to Discover, Onboard, Segment, Vault, Authenticate and Audit privileged accounts and services for your On-premise, SaaS and Cloud Infrastructure assets.
From vaulting credentials for service accounts to managing secrets and API keys for Non-Human Identities, Abira’s advisory services helps organizations navigate the complex vendor landscape and converging security domains of PAM, CIEM, NHI, ITDR/ISPM and IGA.
Abira’s trusted partners include, but are not limited to, CyberArk, Delinea, BeyondTrust, Britive, Hydden, Saviynt other emerging PAM technologies.
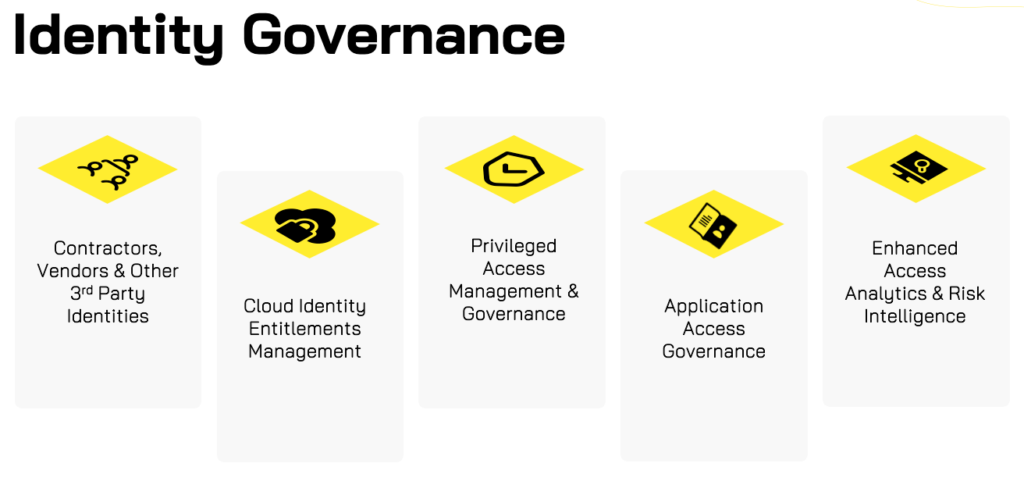
Identity Governance and Administration
Providing the right people with the right access to the right resources at the right time for the right reasons is the core of Abira’s IGA philosophy. With deep expertise in Identity Governance, Abira helps organizations implement Birth-Right and Role-based Identity Lifecycle Management, Intelligent Access Reviews and Exception-based Access Requests to govern and automate access for all Identities – Carbon & Silicon.
With experts across Saviynt, SailPoint, Lumos, Conductor1, CyberArk’s Zilla Security and other IGA solutions, Abira helps organizations meet the ever changing and challenging regulatory compliance controls with integrated Separate of Duties Management & Cloud Infrastructure Entitlements management to meet SOX, HIPAA, SOC2, NYDFS and many other security controls.